Philippine National Public Key Infrastructure (PNPKI)
Public Key Infrastructure (PKI) allows users of public networks like the Internet to exchange private data securely. PKI is essentially a set of hardware, software, policies, personnel and procedures needed to create, manage, distribute, use, store and revoke digital certificates. The PKI is one of the core services being offered by the Department of Information and Communications Technology (DICT) that will foster trust in the government by ensuring secure and reliable online transactions.
All government online applications stand to benefit from the use of the PKI, ultimately improving the delivery of government services to citizens. At the heart of the PKI is the concept of digital certificates. These certificates are very small files that can be stored on your computer, an ordinary flash drive or USB token. Through the use of certificates issued and digitally signed by a Certificate Authority (CA), the PKI authenticates the data source and ensures data had not been tampered with in transit. PKI can also be used to encrypt data such as email or online transactions.
If your agency uses email communication or has online transactions with other agencies or the public, or if your agency plans to do so, then you need PKI. Among the applications that use PKI are:
- Document Signing Applications, e.g. Adobe Reader, Foxit Reader, etc.
- Email Applications, e.g. Outlook, Thunderbird, etc.
Some applications, such as email, are fairly easy to configure and integrate with PKI. These applications only require the users to register and receive their digital certificates. More complicated applications, such as those used for online transactions, would require extended development time. Eventually, digital certificates will be issued to private individuals to facilitate transactions with government as well as to secure their personal electronic communication. Wouldn’t it be nice if we can file our income tax returns online, bid on government procurement proceedings, apply for loans, and pay our taxes in the convenience of our home, knowing full well that our transactions are secure and tamper-proof? All these applications require the PKI, and it is only a matter of time before they become a reality.
PNPKI SERVICES
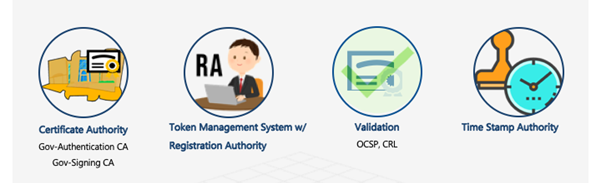
- Certificate Authority & Registration Authority services
These include processing of applications, issuance of digital certificates, and provision of technical support and assistance
- Validation Authority service
This is used by applications to check validity of certificates via Online Certificate Status Protocol (OCSP)/Certificate Revocation List (CRL)
- Timestamping service
This is used by applications to connect to an authoritative time source for the embedded timestamp in a digitally-signed document
WHO CAN AVAIL
- Government agencies and personnel
- Private individuals
- Government computers, servers and machines
BENEFITS
- Vastly improves verifiable identification of an individual or entity
Passwords are often, if not exclusively, used to authorize access to computer systems and applications. A password, even one with a 10-character length, only provides 80-bits of security, and inconvenient discipline must be imposed on users so the passwords they create are not easily breached. A Digital Certificate issued by the PKI will have at a minimum of 2048-bit system generated key to further ensure user identity. This is actually an oversimplified comparison since the complex computations add significant obstacles to those that would compromise a Digital Certificate.
- Digital Certificates imbue on to data sufficient integrity for acceptance as evidence in a court of law
The Philippines, United States, Canada, Korea, Singapore and Malaysia already have laws which provide the legal framework for formally recognizing digitally signed data as proper evidence for courts.
This allows a document in digital form to be signed as if it were a paper document. Moreover, the “signing” also makes the document tamper-proof since the smallest change (1-bit) will be detected upon verification.
- Provides significant protection against unauthorized access of common communications
The government already relies on Information and Communications Technology (ICT) and this is increasing. ICT, however, cannot be secured by traditional methods because of their very nature. Encryption methods being used are not regulated. Moreover, the use of ICT by criminals and enemies of the state requires that legitimate users employ similar, if not better, technologies to keep ahead. To put the PKI’s 4096-bit capability into perspective, Wi-Fi at most can use a 14-character or 96-bit “password” by which to encrypt traffic.
For further inquiries, please email the respective PNPKI Team in your region. Their email addresses are available on the Contact Information tab.
What is Public Key Infrastructure (PKI)?
The Public Key Infrastructure (PKI), as its name implies, is an infrastructure that secures communications among individuals and government agencies. This way, the government’s delivery of services to citizens and businesses becomes safer, faster and more efficient.
Why is it called ‘public key’? Does it mean open and unrestricted?
No. The public key in PKI refers to the virtual ‘key’ that subscribers use to secure files sent over an otherwise unsecure ‘public’ network like the Internet. While it is called public, it can also work in a private network setting.
Why do I need a PKI?
As more people rely on online applications over unsecured networks such as the Internet, the need to secure files and ensure the integrity of information continues to grow. This is where the PKI comes in. It addresses the issue of authenticity, confidentiality and integrity of information.
What is a digital certificate?
A digital certificate is a file issued by a Certificate Authority containing the user’s personal information just like an ordinary ID, only in this case, it is digital.
How can I have a digital certificate?
You can have a digital certificate by personally submitting an application to a Registration Authority (RA). The RA will then ask the Certificate Authority to generate a key or code and give it to you after processing.
Do I have to pay for it?
No. The digital certificate is free.
Where can I use a digital certificate?
You can use a digital certificate in your email and other documents. You can use it to encrypt a document and/or digitally sign it. Its use is to authenticate documents or put signatures on them or both
How do I use a digital certificate?
People need a digital certificate to send you an encrypted email, for instance, that only you can open. They also use it to verify your digital signature on electronic documents. It is not the certificate that you need to protect but the private key that is associated with it. Hence, in cryptographic tokens, the private key is generated in the token and cannot be extracted from it. Soft tokens however store this private key as an ordinary electronic file. It is usually encrypted and the encryption is computationally infeasible to break. Nonetheless, this private key, if someone gets a copy of it and also the passphrase to use it, can be used along with the digital certificate to fraudulently sign documents or open encrypted email.
Do I have an option not to use it?
Of course, you do. It’s just that you will not be able to do the following: open encrypted files, access applications that require digital certificates and digitally sign documents for authenticity.
When can I use a digital certificate?
Whenever you feel like it. Or every time secure communication is needed, or a digital certificate is required for authenticity, confidentiality and integrity of data.
Who can avail of a digital certificate?
Any individual who is of age and possesses the necessary documents (as stated in the application form) may apply for a digital certificate.
Can I apply for other people’s certificate?
No, since personal appearance is needed in the application process.
Where can I use a digital certificate?
A digital certificate can be used in online transactions, in documents, digital signatures, in office applications and in software developed in-house.
How long can I use the digital certificate?
A digital certificate is valid for up to two years. After that, you have to apply for a new one.
How do I renew and how long is the process of renewal?
A digital certificate, technically, cannot be ‘renewed.’ It means you have to apply for a new one every time it expires and go through the application process again. All requirements will have to be satisfied and personal appearance is required.
Where can I store the digital certificate?
It can be stored in a USB secure token, an ordinary USB flash disk, a PC, a laptop or any mobile computer. The USB secure token is the safest because it has a built-in application that allows only a limited number of times for entering the PIN before it is blocked. A token can contain up to ten (10) certificates. Setting the token in the factory default will erase all data in its memory.
What types of certificates are issued?
You can avail of the following types of certificates: Authentication certificate – used in applications that require the user to login. It can be used to encrypt email. Signing certificate – used to digitally sign documents. SSL certificate – a certificate for machines, like web servers, application servers, routers, Wi-Fi devices, and others. (This is not yet available as of this writing.)
What if I lose my certificate?
The digital certificate is a public document. The moment you use it you can never lose it. However, if the private key is lost, compromised or the passphrase to use it is forgotten, then the certificate needs to be revoked and a new key can be generated as well as the digital certificate that will be associated with it.
What if the subscriber resigns, retires or exits from government service?
If it is a soft token, surrendering it is not necessary. The revocation can be easily done by the CA. However, if it is a cryptographic token and the company or CA owns it, then it needs to be surrendered. Individual owners may continue to use the certificates for transactions outside the concerned agency.
What are my responsibilities as digital certificate holder?
You have the responsibility to protect the certificate from misuse and abuse. You cannot, for example, lend it to other people or use it to forge documents or commit illegal acts with it. Unauthorized and illegal use are punishable according to the severity of the offense. A policy will be issued detailing the punishment for each administrative or criminal offense committed in the use of a digital certificate.
How long is the application process?
Upon completion of all the requirements by the applicant, a verification process will start. This process will take a minimum of one day and a maximum of two days, depending on the completion of requirements. After submission of documents (complete), the certificate is issued within a day or two. According to the policy (Section 4.2.3 of the RootCA-CP), issuance of the digital certificate should not exceed five calendar days after successful identity verification.
Is it possible to have multiple certificates?
A person may have two digital certificates: one for authentication and another for digital signing. He or she may get a third certificate, which is still to be offered, for PKI-enabled machines.
How big is a digital certificate?
A digital certificate takes up only 7kb to 10kb of computer memory.
What is the best browser to use when using PKI?
Firefox is recommended as it works well with Java, which is needed to run the digital certificates. Google Chrome, on the other hand, usually can’t recognize Java.
What is the best email provider to use when encrypting and signing emails?
It is recommended to use email providers, such as Thunderbird and Outlook, for your digital certificates.
For further inquiries, please email the respective PNPKI Team in your region. Their email addresses are available on the Contact Information tab.
Individual Certificate
Registration Authority (RA) shall ensure that information and submitted requirements are verified prior to the approval of PNPKI application:
NEW APPLICATIONS:
1. Complete registration at the Online Registration System (ORS) portal
2. Unretouched passport-size colored photograph with plain background taken within the last six (6) months
3. Tax Payer Identification Number (TIN)
4. Mobile phone number
5. Official work email address that can be accessed only by the applicant
6. One (1) primary or two (2) secondary government-issued IDs
7. Consent to verify and share the information submitted (included in the application form).
RENEWAL APPLICATION:
1. Duly accomplished application form;
2. Same requirements as new application
3. Online identity verification (via video call)
o Note: Please send complete application requirements to info.pnpki@dict.gov.ph for NCR or the respective PNPKI Regional Office.
* In the absence of UMID-compliant card, ANY TWO of the following cards are allowed as valid IDs based on BSP Circular 608 series of 2008
List of Accepted Valid IDs:
A. Primary IDs:
● Philippine National ID (PhilID)
● Philippine Passport
● SSS Unified Multi-Purpose ID (UMID)
● LTO Driver’s License
● Professional Regulation Commission (PRC) ID
● Postal Identity Card
B. Secondary IDs:
● Philippines-issued Birth Certificate
● National Bureau of Investigation (NBI) Clearance
● Police Clearance
● Seaman’s Book
● COMELEC Voter’s ID
● OSCA Senior Citizen Card
● Overseas Workers Welfare Administration (OWWA) ID
● Department of Social Welfare and Development (DSWD) Certification
● Integrated Bar of the Philippines ID
● Certification from the National Council for the Welfare of Disabled Persons (NCWDP).
● Government Office and GOCC ID, e.g. Armed Forces of the Philippines (AFP ID), Home Development Mutual Fund (HDMF ID)
● Company IDs Issued by Private Entities or Institutions Registered with or Supervised or Regulated either by the BSP, SEC, or Insurance Commission (IC)
C. For Alien Applicants:
● Valid Passport
● Alien Certification of Registration/Immigrant Certificate of Registration
● Company IDs Issued by Private Entities or Institutions Registered with or Supervised or Regulated either by the BSP, SEC, or Insurance Commission (IC)
For bulk application and further inquiries, please email the respective PNPKI Team in your region. Their email addresses are available on the Contact Information tab.
Agency Certificate
Authentication of Organization Identity
Juridical applicant’s information shall be verified with prior submission of the following:
New Applications:
1. Complete registration at the Online Registration System (ORS) portal
2. Softcopy of the following supporting documents of the authorized representative:
a. Philippine National ID (PhilID/ePhilID) or
b. One (1) primary or two (2) secondary government-issued IDs
c. Unretouched passport-size colored photograph with plain background taken within the last six (6) months
3. Online identify verification with the authorized representative (via video call);
4. Tax Payer Identification Number (TIN) of the Agency;
5. Authorization Letter/Board Resolution naming the authorized representative/s to apply for a digital certificate in behalf of the agency;
6. Verified e-mail address owned by the organization or authorized by the owner of the e-mail address to be used by the organization.
7. Consent to verify and share the information submitted (included in the application form).
Additional Requirements:
For a government agency:
1. Government Service Insurance System (GSIS) registration number
For non-government entities:
1. Securities and Exchange Commission (SEC) business registration for corporation and partnership, DTI Certificate of Business Name Registration for single proprietorship or Cooperative Development Authority (CDA) registration for cooperatives;
2. Business Permit issued by the Local Government Unit (LGU); and
3. Social Security System (SSS) Employer Clearance
RENEWAL APPLICATION:
- Duly accomplished application form;
- Same requirements as new application
- Online identity verification (via video call)
- Note: Please send complete application requirements to
- for NCR or to the respective
* In the absence of a UMID-compliant card, ANY TWO of the following cards are allowed as valid IDs based on BSP Circular 608 series of 2008
List of Accepted Valid IDs:
A. Primary IDs:
● Philippine National ID (PhilID)
● Philippine Passport
● SSS Unified Multi-Purpose ID (UMID)
● LTO Driver’s License
● Professional Regulation Commission (PRC) ID
● Postal Identity Card
B. Secondary IDs:
● Philippines-issued Birth Certificate
● National Bureau of Investigation (NBI) Clearance
● Police Clearance
● Seaman’s Book
● COMELEC Voter’s ID
● OSCA Senior Citizen Card
● Overseas Workers Welfare Administration (OWWA) ID
● Department of Social Welfare and Development (DSWD) Certification
● Integrated Bar of the Philippines ID
● Certification from the National Council for the Welfare of Disabled Persons (NCWDP).
● Government Office and GOCC ID, e.g. Armed Forces of the Philippines (AFP ID), Home Development Mutual Fund (HDMF ID)
● Company IDs Issued by Private Entities or Institutions Registered with or Supervised or Regulated either by the BSP, SEC or IC
C. For Alien Applicants:
● Valid Passport
● Alien Certification of Registration/Immigrant Certificate of Registration
● Company IDs Issued by Private Entities or Institutions Registered with or Supervised or Regulated either by the BSP, SEC, or Insurance Commission (IC)
For further inquiries, please email the respective PNPKI Team in your region. Their email addresses are available on the Contact Information tab.
Digital Certificate Subscriber Agreement
PLEASE READ THIS AGREEMENT CAREFULLY BEFORE USING THE DIGITAL CERTIFICATE ISSUED TO YOU OR YOUR ORGANIZATION. BY APPLYING FOR A DIGITAL CERTIFICATE, YOU ARE AGREEING TO BE BOUND BY THE TERMS OF THIS AGREEMENT. IF YOU HAVE PROBLEMS UNDERSTANDING THIS AGREEMENT, E-MAIL US AT 𝐚𝐥𝐛𝐚𝐲.𝐩𝐧𝐩𝐤𝐢@𝐝𝐢𝐜𝐭.𝐠𝐨𝐯.𝐩𝐡.
1.0 Definitions
Applicant: The individual that applies for (or seeks renewal of) a Digital Certificate naming it as the “Subject”.
Certification Practice Statement (CPS) – A statement of the practices that a certification authority employs in issuing, managing, revoking, and renewing or re-keying certificates.
Certificate Policy (CP) – A named set of rules that indicate s the applicability of a certificate to a particular community and/or class of application with common security requirements. For example, a particular CP might indicate applicability of a type of certificate to the authentication of parties engaging in business-to-business transactions for the trading of goods or services within a given price range.
Certificate Revocation List (“CRL”): A collection of electronic data containing the list of serial numbers revoked or suspended by the Certificate Authority
Online Certificate Status Protocol (“OCSP”): An Internet Protocol (IP) used to obtain the real time revocation status of a digital certificate. It is used as an online faster alternative to CRL list.
Public Key – A mathematical key which is available publicly and which is used to verify Digital Signatures created with the matched Private Key and to encrypt electronic data which can only be decrypted using the matched Private Key
Private Key: A mathematical key which is kept private to the owner and which is used to create Digital Signatures or to decrypt electronic data
Registration Authority (RA) – An entity that is responsible for one or more of the following functions: the identification and authentication of certificate applicants, the approval or rejection of certificate applications, initiating certificate revocations or suspensions under certain circumstances, processing subscriber requests to revoke or suspend their certificates, and approving or rejecting requests by subscribers to renew or re-key their certificates. RAs, however, do not sign or issue certificates (i.e., an RA is delegated certain tasks on behalf of a CA).
Subscriber – A subject of a certificate who is issued a certificate.
2.0 Authority to Use Digital Certificates
2.1 Grant of Authority
As from the Effective Date up to the validity period of any issued Digital Certificate (“Valid from” date to “Valid to” date) , PNPKI grants to the Subscriber the authority to use the requested Digital Certificate in conjunction with Private Key and/or Public Key operations. The obligations of the subscriber (see section 4.0) with respect to Private Key protection are applicable from the effective date.
2.2 Limitations on Authority
The digital certificate cannot be used for purposes other than what is allowed in this subscriber agreement and the CPS.
3.0 Use of PNPKI Digital Certificate
The subscriber shall use the certificate for its lawful and intended use only. The certificate shall be used in accordance with its Key-Usage field extensions. All issued certificate by PNPKI cannot be used for purposes other than what is allowed in this subscriber agreement and by the CPS. PNPKI shall not be liable for any claims arising from prohibited use.
3.1 Acceptance of a Digital Certificate
The following conduct constitutes certificate acceptance:
a) A certificate shall be deemed accepted when it is in the subscriber or representative’s control;
b) Failure of the subscriber to object to the certificate or its content within five (5) calendar days; or
c) The subscriber uses the certificate.
3.2 Revocation of Digital Certificates
A certificate shall be revoked when the bind between the subject and the subject’s public key is no longer valid.
An end-user subscriber certificate can be requested for revocation under any of the following conditions:
a) When a verified request for revocation is received by PNPKI CA or RA;
b) When any of the information found in the certificate is changed or no
longer applicable;
c) When the Private Key, or the media holding the Private Key, associated with the certificate is compromised;
d) When the PNPKI CA determines that the end-user entity is no longer complying with the requirements of by the CPS and this subscriber agreement; or
e) When the PNPKI CA has the reason to believe that the certificate was issued in a manner that is not in accordance with the procedures required by the CPS and this subscriber agreement.
g) When subscriber requested revocation of the Certificate;
4.0 Subscriber Obligations
This Agreement governs the subscriber’s application for, acceptance, and use of, a digital certificate issued by the RA.
a. The provisions of the Root CA CP/CPS, GovCA CP/CPS, and other pertinent documents are binding upon the subscriber.
b. All the information provided in the digital certificate application form is true and correct.
c. The use of the digital certificate shall be for the sole use of the subscriber.
d. The subscriber will not, under any circumstances, allow any other person to use the digital certificate. Any such use by another person constitutes a compromise of the associated private key, requiring the revocation of the digital certificate.
e. The subscriber shall protect the confidentiality of the private key associated with his or her digital certificate as well as any PIN number or other means used to activate the private key.
f. The subscriber shall remain solely responsible for the maintenance of the confidentiality of the certificate.
g. The subscriber shall not use the digital certificate for any unlawful purpose, or for any purpose that does not have anything to do with accessing the PKI information systems or transactions using the digital certificates.
h. The subscriber shall promptly request the RA to revoke the digital certificate upon knowing or suspecting inaccurate information, loss, exposure or compromise of the associated private key.
i. The subscriber shall not tamper, interfere with, or reverse-engineer any technical implementation of the digital certificate or its use, or in any manner seek to compromise the security provided by the RA and the National PKI system.
j. The subscriber accepts the risk of an undetected compromised digital certificate or associated private key, which may be used to impersonate the said subscriber.
5.0 Permission to Publish Information
The Subscriber agrees that PNPKI may publish the serial number of the Subscriber’s Digital Certificate in connection with PNPKI’s dissemination of CRL’s and OCSP.
6.0 Disclaimer
PNPKI shall not be liable for any claims arising from prohibited use of Digital Certificates issued by GovCA. PNPKI will not be liable if the user has not respected his obligations mentioned in the CPS and in this agreement.
7.0 Term and Termination
This agreement shall terminate upon
(a) The expiry date of any Digital Certificate issued to the Subscriber
(b) Any failure to comply with any of the subscriber obligations mentioned in this Subscriber Agreement
8.0 Effect of termination
Upon termination of this Subscriber Agreement for any reason, PNPKI may revoke the Subscriber’s Digital Certificate in accordance with PNPKI revocation procedures.
9.0 CP and CPS Information
The digital certificate contains information provided by the subscriber, which is authenticated by the RA in accordance with the requirements set out in the CA CP and CPS, available for viewing and download at dict.gov.ph/pnpki/.
For a copy of the document click the link below:
PNPKI Certificate Policy Version 2.0
Republic of the Philippines
Department of Information and Communications Technology
18 January 2017
DEPARTMENT CIRCULAR
NO. 2017 – 001
TO : ALL HEADS OF DEPARTMENTS, BUREAUS, OFFICES AND OTHER AGENCIES OF THE NATIONAL GOVERNMENT, INCLUDING CONSTITUTIONAL COMMISSIONS, CONGRESS, THE JUDICIARY, OFFICE OF THE OMBUDSMAN, STATE UNIVERSITIES AND COLLEGES, GOVERNMENT-OWNED OR -CONTROLLED CORPORATIONS, LOCAL GOVERNMENT UNITS AND ALL OTHERS CONCERNED
SUBJECT : AMENDING THE PHILIPPINE NATIONAL PUBLIC KEY INFRASTRUCTURE (PNPKI) ROOT CERTIFICATION AUTHORITY CERTIFICATE POLICY VERSION 1.0
SECTION 1. BACKGROUND AND RATIONALE
1.1 Execuctive Order (E.O.) No. 810, series 2009 institutionalized the certification scheme for digital signatures and directed the application of digital signatures in e-Government Services.
1.2 Section 3(a) of E.O. No. 810, s2009 designated the National Computer Center (NCC) to operate the Philippine Root CA (RootCA).
1.3 Section 15 of Republic Act No. 10844 abolished NCC and transferred its powers and functions, applicable funds and appropriations, records, equipment, property and personnel to the Department of Information and Communications Technology (DICT).
1.4 ICT Office Memorandum Circular No. 2013-001 approved the PNPKI Certificate Policy (CP) version 1.0 in operating the Philippine RootCA.
SECTION 2. PURPOSE
This Department Circular is being issued to amend the PNPKI Certificate Policy version 1.0 issued by the Information and Communications Technology Office (ICT Office) last 23 December 2013.
SECTION 3. COVERAGE
3.1 This Department Circular shall cover all Departments, Bureaus, Offices and Other Agencies of the National Government, including Constitutional Commissions, Congress, the Judiciary, Office of the Ombudsman, State Universities and Colleges, Government-Owned or -Controlled Corporations, Local Government Units.
3.2 The implementation of this Department Circular shall also cover private entities that will make use of the services of the Philippine RootCA.
SECTION 4. APPROVAL OF THE PNPKI CP
The attached PNPKI CP version 2.0 is hereby approved and to be implemented in operating the Philippine RootCA in compliance with Section 3(a) of E.O. No. 810, s2009.
SECTION 5. ADMINISTRATION OF THE PNPKI CP
The administration and updating of the PNPKI CP shall be the responsibility of the PNPKI Team under the DICT.
SECTION 6. REPEALING CLAUSE
All other Circulars and Issuances or parts thereof that are inconsistent with this Department Circular are hereby repealed or modified accordingly.
SECTION 7. EFFECTIVITY
This Department Circular shall take effect immediately upon filing three (3) certified true copies with the Office of the National Administrative Register, University of the Philippines Law Center and publication in a newspaper of general circulation.
APPROVED.
(Sgd.) RODOLFO A. SALALIMA
Secretary
Download a copy of the DC for PNPKI CP
Attachment: PNPKI CP Version 2.0
Certificate Practice Statement Version 1.0
December 23, 2013
Memorandum Circular No. 2013-002
Series of 2013
FOR: ALL HEADS OF THE NATIONAL GOVERNMENT DEPARTMENTS / AGENCIES / BUREAUS, GOVERNMENT-OWNED AND ‑CONTROLLED CORPORATIONS; GOVERNMENT FINANCIAL INSTITUTIONS; STATE UNIVERSITIES AND COLLEGES; LOCAL GOVERNMENT UNITS; CONSTITUTIONAL BODIES, HOUSE OF REPRESENTATIVES, THE SENATE AND THE JUDICIARY
SUBJECT: APPROVAL OF THE PHILIPPINE NATIONAL PUBLIC KEY INFRASTRUCTURE (PNPKI) CERTIFICATION AUTHORITY (CA) CERTIFICATION PRACTICE STATEMENT (CPS) VERSION 1.0
SECTION 1. APPROVAL OF THE PNPKI CA CPS
The attached PNPKI CA CPS version 1.0 is hereby approved and to be implemented in operating the PNPKI CA in compliance with Section 3(b) of E.O. 810 series of 2009.
SECTION 2. ADMINISTRATION OF THE PNPKI CPS
The administration and updating of the PNPKI CA CPS shall be the responsibility of the PKI component team of the iGovPhil Program until the DOST‑ICT Office Rationalization Plan is fully implemented. The responsibility of updating the PNPKI CA CPS shall then be lodged with the Policies and Standards Division under the National ICT Governance Service.
SECTION 3. DIRECTIVE TO THE DOST-ICT OFFICE RECORDS OFFICER
The DOST‑ICT Office Records Officer is hereby ordered to furnish three (3) certified true copies of this Memorandum Circular and the attached PNPKI CA CPS version 1.0 to the University of the Philippines Law Center.
SECTION 4. EFFECTIVITY.
This Memorandum Circular shall take effect immediately.
Recommending Approval:
(Sgd.) DENIS F. VILLORENTE
iGovPhil Program Director
Approved By:
(Sgd.) LOUIS NAPOLEON C. CASAMBRE
Executive Director
DOWNLOAD a copy of the MC for PNPKI CPS.
Attachment: PNPKI CPS Version 1.0
GovRA Accreditation Guidelines
April 25, 2014
MEMORANDUM CIRCULAR NO. 2014-001
Series 2014
FOR: GOVERNMENT AGENCIES WANTING TO BECOME A GOVERNMENT REGISTRATION AUTHORITY (GOVRA)
SUBJECT: PRESCRIBING POLICIES AND PROCEDURES GOVERNING THE ACCREDITATION OF GOVERNMENT REGISTRATION AUTHORITIES UNDER THE NATIONAL CERTIFICATION SCHEME FOR DIGITAL SIGNATURES
Pursuant to the provisions of Executive Order No. 810 issued on 15 June 2009 and entitled, “Institutionalizing the Certification Scheme for Digital Signatures and Directing the Application of Digital Signatures in E-Government Services,” this Memorandum Circular is hereby prescribed by the National Computer Center (NCC), in its capacity as Government Certification Authority (GovCA), for the compliance, information, and guidance of all concerned:
Section I OBJECTIVES
This Memorandum Circular prescribes the POLICIES AND PROCEDURES governing the accreditation of government agencies as Government Registration Authorities (GovRAs) under the National Certification Scheme for Digital Signatures as mandated under Executive Order No. 810, Series of 2009.
Section II DEFINITION OF TERMS
- Accreditation and Assessment Body – refers to the body that accredits the Certification Authorities (CAs) and conducts regular assessment of such CAs to ensure compliance to prescribed criteria, guidelines and standards; refers to the Philippine Accreditation Office (PAO), under the Department of Trade and Industry (DTI);
- Certificate – an electronic document issued to support a digital signature, which purports to confirm the identity or other significant characteristics of the person who holds a particular key pair. Certificates issued may be for general use or for specific use only;
- General Certificate – a certificate which can be used for all government and private transactions;
- Specific Purpose Certificate – a certificate which can only be used for a specific purpose;
- Certificate Revocation List (CRL) – a time-stamped list that identifies/ contains revoked or invalid certificates. The CRL is signed by a Certification Authority and is published periodically in a public repository;
- Certification Authority (CA) – issues digitally-signed public key certificates and attests that the public key embedded in the certificate belongs to the particular subscriber as stated in the certificate. A CA may be involved in a number of administrative tasks such as end-user registration, although these tasks are often delegated to the Registration Authority (RA). The CA may either be a government body or private entity;
- Digital Signature – refers to an electronic signature consisting of a transformation of an electronic document of an electronic data message using an asymmetric or public cryptosystem, such that a person having the initial untransformed document and the signer’s public key can accurately determine: (i) whether the transformation was created using the private key that corresponds to the signer’s public key; and (ii) whether the initial digital document had been altered after the transformation was made;
- Government Certification Authority (GovCA) – refers to the government body that issues digitally-signed public key certificates and attests that the public key embedded in the certificate belongs to the particular subscriber as stated in the certificate. The GovCA designates Government Registration Authorities (GovRAs) and conducts regular assessment of such GovRAs to ensure compliance to prescribed criteria, guidelines and standards. The GovCA is part of ICTO;
- Government Registration Authority (GovRA) – refers to a government agency designated by the Certification Authority (CA) to perform administrative tasks such as end-user registration;
- Root Certification Authority (Root CA) – issues and manages certificates to government and private CAs; the Root CA is part of ICTO;
- Subscriber – an individual or entity applying for and using digital certificates issued by the CA;
- Personal Information Controller – means a person or organization who controls the collection, holding, processing or use of personal information. It includes a person or organization who instructs another person or organization to collect, hold, process, use, transfer, or disclose personal information on his or her behalf, but excludes a person or organization who performs such functions as instructed by another person or organization. It also excludes an individual who collects, holds, processes or uses personal information in connection with the individual’s personal, family or household affairs.
Section III GOVERNMENT REGISTRATION AUTHORITY ACCREDITATION
GovRA accreditation is granted following the mandatory evaluation of an applicant-government agency’s compliance with this Circular. Certification shall be valid for three (3) years, unless suspended or revoked sooner, and subject to the mandatory annual assessment of compliance.
Section IV. CONDITIONS FOR ACCREDITATION FOR GOVRA
- Certification shall be valid for three (3) years unless suspended or revoked sooner, and subject to the mandatory annual assessment of compliance;
- The GovRA-applicant must fulfill basic technical agency requirements before or during the certification process. The full list of technical agency-related requirements is attached as Annex A, which shall form an integral part of this Memorandum;
- Application for accreditation
a) The GovRA-applicant shall send an application letter to the GovCA outlining their objectives in applying for the position of GovRA and their intended subscribers;
b) On receipt of the application letter and the accomplished application form, the GovCA shall acknowledge the application within nine (9) calendar days and direct the applicant-government agency to complete the following required documents within thirty (30) calendar days for document review. The required documents shall form part of the criteria used to evaluate the applicant-agencies, and shall be discussed in detail on Article V:
i. Certified copy of charter / legal document creating the agency and any amendments;
ii. Disaster recovery and business continuity plan;
iii. GovRA operations manual;
c) If the GovRA-applicant is not able to respond to submission of the required documents within the specified number of days stated above, the processing of the application shall be terminated. However, the GovRA-applicant may still reapply for GovRA accreditation;
- Document Review
a) The GovCA shall undertake the review of the submitted documents. Results of the review are communicated to the GovRA-applicant for any clarifications or concerns regarding the submitted documents;
b) The GovRA-applicant must address the concerns raised by the document reviewer within five (5) days. All the required documents need to be approved before an applicant government agency is accredited as a GovRA.
- Preparation for Assessment
a) An assessment team shall be appointed by the GovCA to conduct an on-site assessment of the GovRA-applicant premises;
b) The assessment team shall sign an Impartiality and Confidentiality Statement before conducting the assessment;
- Conduct of Assessment
a) The date of assessment shall be communicated to the GovRA-applicant prior to the actual assessment and shall be agreed upon by the GovRA-applicant and the GovCA;
b) The assessment shall be done against the requirements of relevant standards and criteria as required by GovCA;
c) During the assessment, the team shall review the policies and procedures of the GovRA-applicant as documented in its Operations Manual and other relevant documents. The team shall also assess the implementation of these operation standards and the overall competence of the GovRA-applicant in their issuance of digital certificates or signatures;
- Evaluation
a) Following completion of document review and on-site assessment, an evaluation shall be conducted by an independent panel assigned by the GovCA;
b) All costs involved in the course of the assessment shall be the responsibility of the GovRA-applicant.
- Recommendation
a) If there are no negative findings raised, the GovRA-applicant shall be recommended for accreditation. Otherwise, the GovRA-applicant shall be given thirty (30) calendar days to rectify the negative findings. If the GovRA-applicant is unable to remediate the negative findings, the application shall be denied;
b) A recommendation letter for accreditation will be issued to the successful GovRA-applicant. A Memorandum of Understanding shall be signed between the GovCA and the (recommendee) successful GovRA-applicant, with the final version of the approved documents evaluated during the accreditation process annexed as part of the memorandum.
- Issuance of Certificate
a) A certificate shall be issued to the successful GovRA- applicant and their information added to the GovCA website;
b) The whole accreditation process is required to be completed within ninety (90) calendar days from the date of submission of documents, otherwise the GovRA-applicant shall need to re-apply;
c) The requirements for certification are a continuing requirement that must be maintained by the GovRA-certified agency for as long as it is functioning as such. The GovCA may revoke the agency’s GovRA status if the GovRA fails to uphold its requirements.
Section V. DOCUMENTARY CRITERIA FOR APPLICANT EVALUATION
Strict compliance with the criteria listed below is mandatory for all government agencies applying for certification to become a GovRA. All approved documents for public use are required to be uploaded and made public to the GovRA website. The following essential documents must be supplied and will be used for evaluation:
- Disaster Recovery and Business Continuity Plan
The Disaster Recovery and Business Continuity Plan is an internal document for the use of GovRA personnel describing how services will be restored in the event of a system crash or failure.
It shall describe the emergency response procedure to be followed in the event of a disaster affecting the function(s) of the GovRA; a security incident or suspected security incident affecting the function(s) of the GovRA. The document shall include mechanisms for the preservation of evidence of system misuse which could be admissible in a court of law.
This internal document is not publicly available and is restricted to ensure that the document is consistent with the information contained in the Security Profile, Operations Manual and the Code of Practice for Information Security Management (ISO/IEC 27002:2005) and the Guidelines for Information and Communications Technology Disaster Recovery Services (ISO/IEC 24762:2008).
- GovRA Operations Manual
The GovRA Operations Manual describes how the GovRA service will be operated and managed on a day to day basis, providing details of the functions and responsibilities of the personnel within the GovRA. It is essentially an internal document for use by the GovRA staff and will also describe the GovRA staffs’ training plan and the Entity Identification process when hiring staff. It will provide directions for the personnel on the implementations of policies and procedures specified in the Security Profile and the Disaster Recovery and Business Continuity Plan.
Section VI. PERSONNEL HIRING REQUIREMENTS
The GovRA hiring practices shall include, as a minimum, the following processes on personnel handling Entity Identification materials:
- Duly accomplished GovRA Employee User Application Form to be submitted to GovCA;
- Police, NBI and Court Clearance;
- Background check;
- Mandatory orientation session with each employee;
- Computer literate;
- Signed non-disclosure agreement between the GovRA and the employee;
- Development and implementation of appropriate training courses for all GovRA employees;
- Orientation course on Electronic Commerce Act of 2000 (R.A. 8792), Executive Order No. 810, Series of 2009, Data Privacy Act of 2012 (R.A. 10173) and Cybercrime Prevention Act of 2012 (R.A. 10175);
- Orientation course on GovRA module, including Overview, Configuration and RA User Operation, and GovCA Certificate Policy and Certification Practice Statement (CPS) to be conducted by the GovCA.
Section VII. SUBSCRIBER-APPLICANT IDENTIFICATION PROCESSING
Identification of the subscribers of Digital Certificates shall be done through the following:
- An individual applicant shall comply with the following for identification:
a) Personal appearance of the applicant;
b) Taxpayer Identification Number (TIN);
c) A Unified Multi-Purpose Identification (UMID)-compliant card. In the absence of a UMID-compliant card, any two of the following cards are allowed as valid IDs based on BSP Circular 608, series of 2008:
i. Passport
ii. Driver’s License
iii. Professional Regulation Commission (PRC) ID
iv. National Bureau of Investigation (NBI) Clearance
v. Police Clearance
vi. Postal ID
vii. Voter’s ID
viii. Government Service Insurance System (GSIS) e-Card
ix. Social Security System (SSS) Card
x. Senior Citizen Card
xi. Overseas Workers Welfare Administration (OWWA) ID
xii. OFW ID
xiii. Seaman’s Book
xiv. Alien Certification of Registration/Immigrant Certificate of Registration
xv. Government Office and GOCC ID, e.g. Armed Forces of the Philippines (AFP ID), Home Development Mutual Fund (HDMF ID)
xvi. Certification from the National Council for the Welfare of Disabled Persons (NCWDP)
xvii. Department of Social Welfare and Development (DSWD) Certification
xviii. Integrated Bar of the Philippines
xix. Company IDs Issued by Private Entities or Institutions Registered with or Supervised or Regulated either by the BSP, SEC or Insurance Commission
d) A passport-sized photo taken within the last six (6) months;
e) Phone number (mobile and/or landline);
f) E-mail address owned by the individual or authorized by the owner for use by the subscriber;
g) Latest copy of a bill showing the physical address of the applicant, where the PIN which will be used to activate a digital certificate shall be mailed; and
h) Consent to verify the information submitted.
- For the juridical applicant:
a) Requests for CA certificates shall include the CA name, address and documentation of the existence of the organization;
b) The PNPKI RootCA or subordinate CA shall verify the information in addition to the authenticity of the requesting representative and the representative’s authorization to act in the name of the CA;
c) A juridical applicant’s information shall be verified with prior submission of the following:
i. Taxpayer Identification Number (TIN);
ii. Authorization Letter or Board Resolution naming up to three (3) authorized representative/s to apply for a digital certificate in behalf of the agency;
iii. Consent to verify the information submitted;
iv. Verified e-mail address owned by the organization or authorized by the owner of the e-mail address to be used by the organization; and
v. Latest copy of a bill containing the address of the applicant where the PIN, which will be used to activate a digital certificate, shall be mailed;
vi. Juridical applicants shall send their applications via authorized representatives who shall comply with all of the requirements for individual applicant;
d) For a government agency:
i. Government Service Insurance System (GSIS) registration number;
e) For non-government agencies:
i. Securities and Exchange Commission (SEC) business registration for corporation and partnership, DTI Certificate of Business Name Registration for single proprietorship, or Cooperative Development Authority (CDA) registration for cooperatives;
ii. Business Permit issued by the Local Government Unit (LGU); and
iii. Social Security System (SSS) Employer Clearance;
f) For organizations requesting SSL Certificates, the following requirements shall be complied:
i. Authorization letter, signed by the head of the organization, naming the authorized representative/s; and
ii. Certification from the Philippine Government Internet Domain Name Registry validating the authenticity of the entity’s domain name or other recognized domain name registry operating in the Philippines recognized by the PNPKI; or any proof of ownership of a particular domain name.
Section VIII. PRIVACY POLICY
The processing of personal information shall be allowed, subject to compliance with the requirements of this Guideline and other laws, in particular R.A. 10173, allowing disclosure of information to the public and adherence to the principles of transparency, legitimate purpose, and proportionality.
Personal information must be:
- Collected for specified and legitimate purposes determined and declared before, or as soon as reasonably practicable after collection, and later processed in a way compatible with such declared, specified and legitimate purposes only;
- Processed fairly and lawfully;
- Accurate, relevant and, where necessary for purposes for which it is to be used the processing of personal information, kept up to date; inaccurate or incomplete data must be rectified, supplemented, destroyed or their further processing restricted;
- Adequate and not excessive in relation to the purposes for which they are collected and processed;
- Retained only for as long as necessary for the fulfillment of the purposes for which the data was obtained or for the establishment, exercise or defense of legal claims, or for legitimate business purposes, or as provided by law; and
- Kept in a form which permits identification of data subjects for no longer than is necessary for the purposes for which the data were collected and processed: Provided, That personal information collected for other purposes may lie processed for historical, statistical or scientific purposes, and in cases laid down in law may be stored for longer periods: Provided, further, That adequate safeguards are guaranteed by said laws authorizing their processing.
The GovRA must ensure implementation of personal information processing principles set out herein.
Section IX. AMENDMENTS TO THE GUIDELINES
The accreditation guidelines outlined in this Circular may change over time to reflect advances in technology and government policies. Any such amendments will be done in consultation with existing accredited GovRAs in accordance with the terms of their existing certification. The time frame for compliance with the new criteria is set to ninety (90) days.
Section X. OTHER APPLICABLE LAWS AND PENALTIES
The use and issuance of digital certificates shall be covered by the provisions of Republic Act No. 8792 or the Electronic Commerce Act of 2000, Republic Act No. 8484 or the Access Devices Regulation Act of 1998 and Republic Act No. 7394 or the Consumer Act of the Philippines and their Implementing Rules and Regulations (IRRs). Hence, violations committed against such laws in relation to the use and issuance of digital certificates shall be subject to the penalties applicable under said laws and their IRRs.
Section XI. DIRECTIVE TO THE DOST-ICT OFFICE RECORDS OFFICER
The DOST-ICT Office Records Officer is hereby ordered to furnish three (3) certified true copies of this Memorandum Circular and the attached annex to the University of the Philippines Law Center.
Section XII. EFFECTIVITY
This Circular shall take effect immediately.
Recommending Approval:
(Sgd.) DENIS F. VILLORENTE
iGovPhil Program Director
Approved By:
(Sgd.) LOUIS NAPOLEON C. CASAMBRE
Executive Director
DOWNLOAD a copy of the Government Registration Authority (GovRA) Accreditation Guidelines
Time Stamping Authority
Memorandum Circular No. 2015-____
Series of 2015
FOR: ALL HEADS OF THE NATIONAL GOVERNMENT DEPARTMENTS, AGENCIES, BUREAUS; GOVERNMENT-OWNED AND -CONTROLLED CORPORATIONS; GOVERNMENT FINANCIAL INSTITUTIONS; STATE UNIVERSITIES AND COLLEGES; LOCAL GOVERNMENT UNITS; CONSTITUTIONAL BODIES; HOUSE OF REPRESENTATIVES; THE SENATE; AND THE JUDICIARY
SUBJECT: APPROVAL AND ADOPTION OF THE PHILIPPINE NATIONAL PUBLIC KEY INFRASTRUCTURE (PNPKI) TIME-STAMPING AUTHORITY – TIME-STAMP POLICY AND PRACTICE STATEMENT (TSA-TSP / PS)
SECTION 1. Approval and Adoption of the PNPKI TSA-TSP / PS
The ICT Office hereby approves and adopts the attached PNPKI TSA-TSP / PS, which addresses the Time-Stamping Services (TSSs) and describes the operational and management policy and practices followed by the PNPKI.
SECTION 2. Administration of the PNPKI TSA-TSP / PS
The administration and updating of the PNPKI TSA-TSP / PS shall be the responsibility of the Policies and Standards Development Division of the ICT Office.
SECTION 3. Repealing Clause
All issuances, orders, rules, and regulations or parts thereof that are inconsistent with the provisions of this memorandum circular are hereby repealed, amended, or modified accordingly.
SECTION 4. Separability Clause
Should any provision of this Memorandum Circular be declared invalid or unconstitutional, the other provisions not affected thereby shall remain valid and subsisting.
SECTION 5. DIRECTIVE TO THE DOST-ICT OFFICE RECORDS OFFICER
The DOST-ICT Office Records Officer is hereby ordered to furnish three (3) certified true copies of this circular and the attached PNPKI TSA-TSP / PS to the University of the Philippines Law Center.
SECTION 6. EFFECTIVITY
This Memorandum Circular shall take effect immediately.
Recommending Approval:
DENIS F. VILLORENTE
Deputy Executive Director for E-Government
Approved By:
LOUIS NAPOLEON C. CASAMBRE
Executive Director
Attachment: Time-stamping Authority – Time-stamping Policy / Practice Statement (TSA-TSP / PS
DOWNLOAD a copy of the Memorandum Circular for PNPKI TSA-TSP / PS
Certificate Chain of Trust
How to Install the PNPKI Certificate Chain of Trust
- For Windows users:
- Close all browsers.
- Unzip the Root CA certificate installer.zip.
- Double click on the setup.exe.
- Click Yes at the User Account control.
- Follow installation procedure then click on Install.
- Wait for it to install then click finish.
- For Mac users:
To download instructions on how to install the PNPKI chain of trust in Mac click the link below:
Certificate Authority (CA) Certificates
to download certificates, right click then save link as
| Philippine PKI CA Certificates – CER Format
SHA256 sum: 8af4bbeb31aecb390b4ff77005c5736f9049a99ce4b93f0008f7fccd9d54a50b |
Revocation Form
If you wish to request for new certificates because your previously issued certificates were compromised, lost, or already unusable, kindly request for revocation of these certificates. To request for revocation, please accomplish and submit the signed revocation form to info.pnpki@dict.gov.ph (NCR) or to the respective PNPKI Regional Office.
PNPKI Certificate Revocation Form.pdf
Please note that revoked certificates are invalid and unusable.
PNPKI Manuals
Tutorial Videos
1. PNPKI INTRODUCTION
Government services can be safer, faster and more efficient with the use of PNPKI. This video features a short introduction into PNPKI and its benefits.
2. Submitting an Online Application Process
Featured here is a video tutorial on how you can apply online for your own digital certificate. A digital certificate is a file that works as a digital ID to ensure your personal information is safe over the Internet.
3. Installing the Digital Certificate
This video will guide you on how to install the Digital Certificate once you receive an email notifying you that they are ready for download.
Optional:
a. Steps for Installing Chain of Trust
Applicants who have completed the registration requirements will receive an e-mail within 2-3 business days containing his/her digital certificate download credentials. This video walks you through the first step on how to install the Digital Certificate Chain of Trust.
b. Process on Requesting for Certificates
This video will guide you through the step-by-step process of getting your Certificate Enrollment and requesting for Signing Certificate.
NOTE: Please be informed that the information shown in the video such as the username and password are only for tutorial video purposes, and we recommend users to refrain from copying this information while applying for YOUR OWN digital certificate.
Moreover, we instruct everyone to carefully review your certificate information before you request for your certificate.
c. Downloading and Installing Certificate
This video will teach you how to create a certificate backup once your request status has been updated to “Issued”.
NOTE: Always check your Inbox for e-mails from the PNPKI team containing links for downloading of files and the login portal. Also, carefully note and remember your password, as the PNPKI team cannot reset the backup password of your certificate.
d. Installing Certificates in Windows Keystore
This video tutorial features the final step for digital certificate registration and focuses on how to install the digital certificate in your Windows Keystore.
4. Digital Signature in a PDF with Adobe Reader
Individuals who have completed the registration process may now use the digital certificate to digitally sign PDF documents using Adobe Acrobat reader and send it via e-mail.
This video features the process of creating the digital signature to sign PDF documents, validating said signature, and adding authoritative timestamps to the PDF file.
PNPKPI Contact Information
For further inquiries and submission of applications (renewal and bulk), please send email to the PNPKI team in your respective area for assistance. Thank you.
| Office | Email Address |
|---|---|
| Albay Provincial Office (PO) | 𝐚𝐥𝐛𝐚𝐲.𝐩𝐧𝐩𝐤𝐢@𝐝𝐢𝐜𝐭.𝐠𝐨𝐯.𝐩𝐡 |
| Camarines Norte PO | 𝐜𝐚𝐦𝐧𝐨𝐫𝐭𝐞.𝐩𝐧𝐩𝐤𝐢@𝐝𝐢𝐜𝐭.𝐠𝐨𝐯.𝐩𝐡 |
| Camarines Sur PO | 𝐜𝐚𝐦𝐬𝐮𝐫.𝐩𝐧𝐩𝐤𝐢@𝐝𝐢𝐜𝐭.𝐠𝐨𝐯.𝐩𝐡 |
| Catanduanes PO | 𝐜𝐚𝐭𝐚𝐧𝐝𝐮𝐚𝐧𝐞𝐬.𝐩𝐧𝐩𝐤𝐢@𝐝𝐢𝐜𝐭.𝐠𝐨𝐯.𝐩𝐡 |
| Masbate PO | 𝐦𝐚𝐬𝐛𝐚𝐭𝐞.𝐩𝐧𝐩𝐤𝐢@𝐝𝐢𝐜𝐭.𝐠𝐨𝐯.𝐩𝐡 |
| Sorsogon PO | 𝐬𝐨𝐫𝐬𝐨𝐠𝐨𝐧.𝐩𝐧𝐩𝐤𝐢@𝐝𝐢𝐜𝐭.𝐠𝐨𝐯.𝐩𝐡 |
Privacy Policy
The Online Registration System (ORS) and PhilSign Mobile Applications of the Philippine National Public Key Infrastructure (PNPKI) are platforms developed that aim to serve the Filipino people by enabling secure and efficient digital transactions, fostering the widespread adoption of secure digital signing, and strengthening trust in electronic processes, particularly in government transactions.

Privacy Notice
The Online Registration System (ORS) and PhilSign Mobile Applications of the Philippine National Public Key Infrastructure (PNPKI) are platforms developed that aim to serve the Filipino people by enabling secure and efficient digital transactions, fostering the widespread adoption of secure digital signing, and strengthening trust in electronic processes, particularly in government transactions. These initiatives are part of the broader mission to promote a digitally empowered society in the Philippines.
At DICT, we recognize the importance of data privacy and are committed to protecting your personal data. In line with this, we ensure that we comply with the Data Privacy Act of 2012 (RA 10173), along with its Implementing Rules and Regulations as well as any other relevant data privacy-related laws and issuances by the National Privacy Commission. Furthermore, we only collect and process information that is necessary to fulfill the purpose of our platform. This Privacy Notice explains what information we collect, process, and share. It also informs you why we do so, and your data privacy rights with regard to your information.
We may update this Privacy Policy to reflect needed changes in our policy to comply with the law. In such cases, we encourage you to check for updates on our Privacy Policy, if notified. This is available on our website or app for your information and reference.
WHAT DATA DO WE COLLECT
The information we collect from the User may either be Personal Information (PI) and/or Sensitive Personal Information (SPI), as defined in the Data Privacy Act of 2012:
Personal Information (PI) is any information from which the identity of an individual can be reasonably and directly ascertained, or when put together with other information would directly and certainly identify an individual, such as name, date, and place of birth, specimen signature or biometrics (fingerprint, face recognition, palm print, etc.), photo, present and permanent address, source of fund or income, name of employer or the nature or self-employment or business, contact details such as personal telephone number, personal mobile number, and official work email address, mother’s maiden name, cookie information, user credentials (i.e., username and password, PIN/MPIN, etc.), contacts list, geolocation, and information about the device you use to interact with us.
Sensitive Personal Information (SPI) is any information that falls under the category of personal information with higher security impact as described in applicable privacy law. This information includes but is not limited to marital status, cardholder data (CVV/CVC, Expiry Date), tax returns, government-issued numbers peculiar to an individual (ex. SSS, GSIS, UMID, etc.), information on IDs issued by private companies that are duly registered with the Securities and Exchange Commission, and student IDs for those who are not yet of voting age (below 18 years old).
The information we collect from our subscribers for the various functions of the platform is as follows:
ORS / PhilSign Mobile Application
Personal Information
● Full Name
● Sex
● Civil Status
● Date and Place of Birth
Organizational Details
● Organization Name & Unit
Residential Address
● Residential Address
● Official Work Email Address
Contact Numbers
● Landline or Mobile Number
Uploading of Required Documents
● Primary Identification
● Secondary Identification
KYC for Users
● Liveness Detection/Verification
By registering their account, users can have full access to the PhilSign Mobile Application.
HOW YOUR PERSONAL DATA IS COLLECTED
We collect your Personal Data when you:
● register in the App;
● provide us with supporting documents to validate your identity;
● disclose your information through phone calls, emails, SMS, or verbal communication with our authorized representatives; and
● visit and contact us through our official contact and/or address.
No information from users will be collected until they have given their express consent. During the initial registration process, clicking the checkbox will signify that the user has read and agrees to the General Terms and Privacy Conditions.
HOW WE USE YOUR PERSONAL DATA
We will only use your Personal Data when needed for the various features of the PNPKI Mobile Applications. We may not process or use your information without your express consent.
Data will be used for the purpose of registering an account within the application and updating their profile accordingly for the e-KYC procedure. Doing this grants them full access to the various features of PNPKI Mobile Applications.
When required by our Privacy Policy and the law and before we use or process your Personal Data for any other purpose, we will ask for your consent.
YOUR RIGHTS AS A DATA SUBJECT
As a subscriber of the PNPKI Mobile Applications, you are entitled to the following data privacy rights:
1. To be informed whether your Personal Information shall be, is being, or has been processed;
2. To reasonably access any Personal Information collected and processed in the duration of usage of the application;
3. To object or withhold consent with regard to the collection and processing of your Personal Data;
4. To suspend, withdraw, or order the blocking, removal, or destruction of Personal Data from the relevant company’s filing system;
5. To dispute the inaccuracy or error in Personal Data, and the relevant company shall correct it immediately and accordingly, upon the request unless the request is vexatious or otherwise unreasonable;
6. To obtain a copy of the data in an electronic or structured format that is commonly used and allows for further use by the Data Subject;
7. To be indemnified for any damages sustained pursuant to the provisions of the Data Privacy Act or other privacy laws.
If you wish to exercise any of the rights set out above or require further information, you may contact us.
CONTACT US
If you have any questions pertaining to this App or any of the Terms and Conditions contained herein, please contact the Digital Certificate Division at 𝐚𝐥𝐛𝐚𝐲.𝐩𝐧𝐩𝐤𝐢@𝐝𝐢𝐜𝐭.𝐠𝐨𝐯.𝐩𝐡 or reach out to any of the PNPKI Regional Offices nationwide.